SOC 2 Type II Compliance Overview
SOC 2 Type II compliance, certified by the American Institute of Certified Public Accountants (AICPA), is a stringent standard focused on ensuring our systems are securely managed with a strong emphasis on protecting client privacy and interests. It is structured around the Trust Services Criteria (TSC), which include five key areas: Security, Availability, Processing Integrity, Confidentiality, and Privacy. These criteria form the basis of our data protection strategy, ensuring we meet and exceed industry standards in every aspect of our operations.

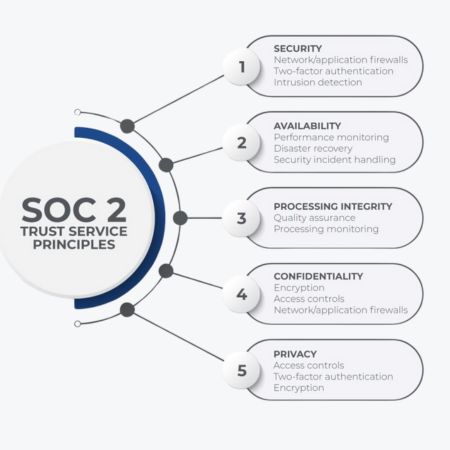
Trust Services Criteria
Security : Implement and maintain controls to prevent unauthorized access, ensuring data integrity and confidentiality. Implement regular security policy updates and employee awareness training.
Availability : Ensure that systems and services are accessible for client use as promised. Implement disaster recovery and business continuity plans to manage potential disruptions.
Processing Integrity : Ensure that system processing is complete, valid, accurate, timely, and authorized. Conduct regular audits and checks to verify data processing integrity.
Confidentiality : Protect confidential information throughout its lifecycle. Use robust encryption and granular access controls to safeguard sensitive information.
Privacy : Protect personal information from collection through disposal. Adhere to privacy practices that comply with legal and regulatory requirements.
Policies and Procedures
Development and Implementation : We have established comprehensive policies and procedures that address each of the Trust Services Criteria. These documents provide a clear framework for managing security, availability, processing integrity, confidentiality, and privacy within our organization. We ensure these policies are not only created but also effectively communicated and accessible to all relevant employees, ensuring everyone understands their role in maintaining compliance and protecting client data.
Periodic Review and Updates : The digital landscape is constantly evolving, and so are the threats to data security. To stay ahead, we regularly review our policies and procedures to ensure they remain effective and relevant. We update our policies to reflect the latest technological advancements, regulatory changes, and industry best practices. This proactive approach ensures that our policies always align with the highest standards of data protection.


Audit and Assurance
Internal Audits : To maintain compliance with SOC 2 Type II criteria, we conduct regular internal audits. These audits thoroughly assess our adherence to the Trust Services Criteria and our internal policies. When non-compliance issues are identified, they are documented and promptly addressed, ensuring continuous improvement in our security controls and processes.
External Audits : We engage independent auditors to perform SOC 2 Type II audits, providing an unbiased evaluation of our compliance. These external audits result in a certification that not only validates our efforts but also offers valuable insights into areas for improvement. We use audit findings to refine our security controls and processes, continually enhancing our ability to protect client data.
Employee Training and Awareness
Regular Training Programs : Security is a shared responsibility, and all employees must be equipped with the knowledge to uphold our high standards. We offer ongoing training programs that cover security policies, procedures, and best practices. These programs are regularly updated to reflect current threats and regulatory requirements, ensuring our team is always prepared to respond effectively.
Awareness Campaigns : Beyond formal training, we run regular awareness campaigns to reinforce the importance of information security. These campaigns engage employees across the organization through workshops, newsletters, and online modules. By keeping security top of mind, we foster a culture of vigilance and responsibility that permeates every level of our organization.


Vendor Management
Contractual Agreements : Include security and confidentiality clauses in all vendor contracts. Ensure vendors comply with SOC 2 Type II requirements.
Ongoing Monitoring: Vendor management continues beyond the initial assessment. Organizations should establish processes for continuously monitoring vendor performance, including reviewing updated SOC 2 Type II reports annually or as they become available.
Incident Response: Vendors should have clear plans that align with SOC 2 Type II criteria. Organizations should ensure these plans are in place and that vendors are prepared to respond to security incidents promptly.